| Version 82 (modified by , 13 years ago) (diff) |
|---|
Startup
In the Startup Guide we describe how to use the mcproxy, how to configurate and check the functionality. We describe three scenarios and discusses where problems could arise.
Tables, Flags and useful Tools
We offer an overfew of the used Linux-Kernel tables and flags by the mcproxy. Also we make mention of a few useful tools to test and analyse the mcproxy.
Tables (IPv4 | IPv6)
The following tables can be found under the path /proc/net/.The ipv6 tables shows the same contain like the ipv4 tables. But they are only available if you configure and compile your own Linux-Kernel. For more details see here.
- igmp | igmp6
- This table shows the multiast group subscriptions of your system for every interface. The multicast group addresses are written in hexadecimal and network byte order (only for IPv4). For example an ip address like FEDCBA98 means 152.186.220.254. The mcproxy subscribe a multicast group on the upstream interface for every subscritption heard on the downstream side. This can be seen in the igmp table.
- ip_mr_vif | ip6_mr_vif
- This table shows interfaces which are registarte to forward multicast traffic. These interfaces are identified by an virtual interface index (vif). All interfaces used by the mcproxy registrated here.
- ip_mr_cache | ip6_mr_cache
- This table shows the multicast forwarding rules. All interfaces used in this table associated with a vif.
Flags
- MRT-Flag
- If the multicast routing flag is set, then the Linux-Kernel is initialse to forward multicast traffic. Only one programm at the same time can set the MRT-Flag to use the multicast routing tables. To set the flag you need root previligies. To change the flag manual you can overwrite the following file:
/proc/sys/net/ipv<X>/conf/default/mc_forwarding
- RP-Filter
- The Reverse Path Filter check the source IP of each packet received on an interface against the routing table. If the best route for the source IP address does not use the same interface that the packet was received on the packet is dropped. If the multicast path is not similar to the ip path, the flag musst be turned off. This is imported for the multicast client and for the mcproxy itself and can be done in the following file:
/proc/sys/net/ipv4/conf/<interface>/rp_filter
Tools
- smcroute
- Smcroute is a command line tool to manipulate the multicast routes of the Linux kernel and it can send join and leave messages to subscribe mutlicast groups. Attention! Smcroute is a daemon and set the MRT-Flag. So you cannot run smcroute and mcproxy on the same system. Here is a link to the project page.
- iperf
- Iperf is a commonly used network testing tool that can create TCP and UDP data streams and measure the throughput of a network that is carrying them. You can use it to send multicast test messages. To install it use the following line of code:
apt-get install iperf
- wireshark/tcpdump
- Wireshark and tcpdump are packet analyzer. They are used for network troubleshooting and analysis. They can be installed with the following comand:
apt-get install wireshark apt-get install tcpdump
Scenarios
1.
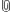
This is the easiest scenario. For example it can be used to forward a multicast IPTV stream from a service provider to your pc or to your flat network. The configuration file of the mcproxy have to look like this:
protocol IGMPv2 eth0 ==> eth1
Or for IPv6:
protocol MLDv1 eth0 ==> eth1
This means the mcproxy use the Groupmembership Protocol IGMPv2 (IPv4) or MLDv1 (IPv6) to subscribe multicast groups and set as upstream the interface eth0 and as downstream eth1. So the mcproxy will forward all multicast streams of the upstream to the downstream if a client in this network subsribe the specific group. On the other side the multicast streams of the downstream will automticly forward to the upstream.
Then you can start the mcproxy with the following command:
sudo mcproxy -svv -c <configfile>
with this option the mcproxy print many status information like this:
protocol:
IGMPv2
eth0 ==>
eth1
alvie time: 1
##-- instance upstream lo [vif=0] --##
group addr
-- downstream eth0 [vif=1] --
group addr | robustness_counter | flag
[0] 224.0.0.251 2 RUNNING
src addr | robustness_counter | flag
[0] 141.22.27.11 2 CACHED_SRC
[0] 224.0.0.251 2
2.
 ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
3.
 ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj ölajsdfölkj
Attachments (3)
- szenarios1b.png (8.8 KB) - added by 13 years ago.
- szenarios2b.png (24.0 KB) - added by 13 years ago.
- szenarios3b.png (18.4 KB) - added by 13 years ago.
Download all attachments as: .zip
